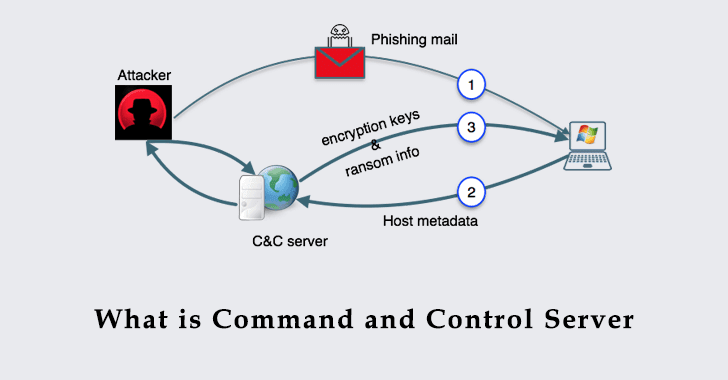
In the vast and intricate web of cybersecurity, Command and Control (C2) servers emerge as pivotal players in the digital shadows. These servers, often shrouded in mystery, are the masterminds behind the strings of cyberattacks that we hear about in the news. But what exactly are these C2 servers, and why are they so crucial to cybercriminals?
At their core, C2 servers are the infrastructure and protocols used by threat actors to manage and coordinate malicious activities. These activities can range from data breaches and malware dissemination to full-scale cyberattacks. The sophistication of C2 infrastructure, including covert communication channels and obfuscation techniques, poses a significant challenge to cybersecurity professionals.
The history of C2 servers is as old as the internet itself. Initially, they were simple setups used to manage and deploy malware, enabling attackers to maintain persistent access to compromised systems. However, as technology advanced, so did the complexity of these servers. Today, they are highly sophisticated and versatile, capable of orchestrating a wide array of cyberattacks, from DDoS assaults to ransomware campaigns.
Understanding how C2 servers operate is like peeling an onion, layer by layer. The setup begins with establishing the servers, which are often hosted on compromised or anonymous servers to evade detection. Threat actors use domain generation algorithms (DGA) to create numerous domain names, helping them avoid blacklisting and tracking by security solutions. Once the initial compromise is in place, the C2 server acts as a puppeteer, pulling the strings of infected devices to execute the attacker’s bidding.
The modern C2 infrastructure employs encryption and obfuscation techniques to conceal communication channels, making detection and attribution a challenging endeavour for defenders. This is where the cat-and-mouse game between cybercriminals and cybersecurity experts becomes most intense. The defenders must constantly evolve their strategies to identify, analyse, and mitigate C2 activity, safeguarding critical systems and data in the process.
So, why should the average person care about C2 servers? Well, in today’s interconnected world, the impact of cyberattacks can be far-reaching, affecting not just corporations but individuals as well. Personal data, financial information, and even national security can be compromised through these attacks. By understanding the role of C2 servers, we can better appreciate the complexities of cybersecurity and the importance of robust defense mechanisms.
As we continue to navigate the digital age, the significance of C2 servers in the landscape of cyber threats cannot be overstated. They are not just a concern for IT departments but for everyone who uses technology. Awareness and education are key to ensuring that we stay one step ahead of the cybercriminals who lurk in the shadows of the internet, waiting for the opportunity to strike.


Leave a comment